AZURE BLUEPRINTS – TUTORIAL

Just as a blueprint allows an engineer or an architect to sketch a project’s design parameters, Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to rapidly build and stand up new environments with trust they’re building within organizational compliance with a set of built-in components — such as networking — to speed up development and delivery.
Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such as:
- Role Assignments
- Policy Assignments
- Azure Resource Manager templates
- Resource Groups
The Azure Blueprints service is backed by the globally distributed Azure Cosmos DB. Blueprint objects are replicated to multiple Azure regions. This replication provides low latency, high availability, and consistent access to your blueprint objects, regardless of which region Blueprints deploys your resources to.
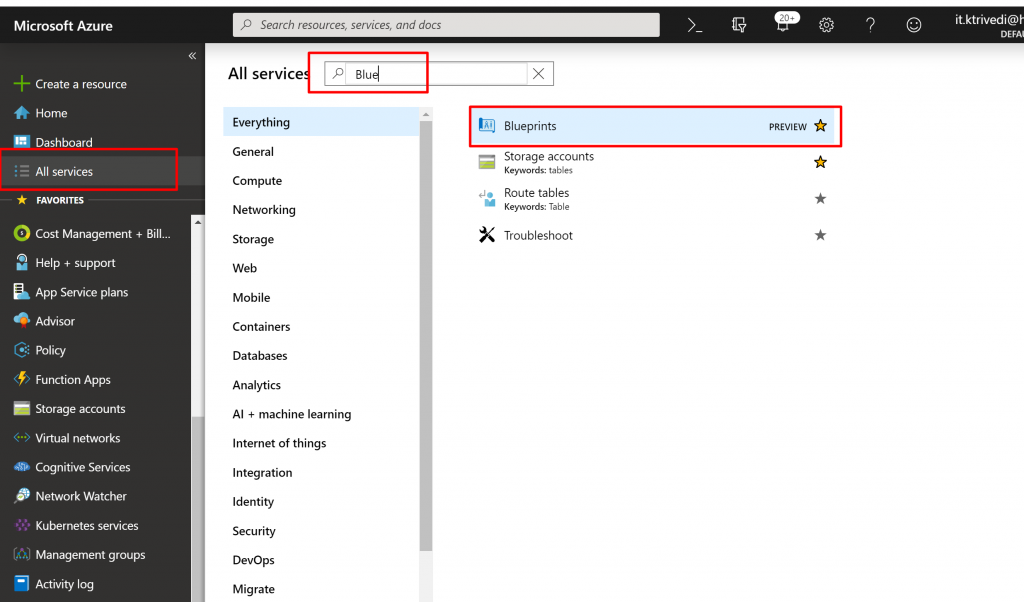
- Open Azure Portal –> Click on All Services –> Search for Blueprints –> and Click on it
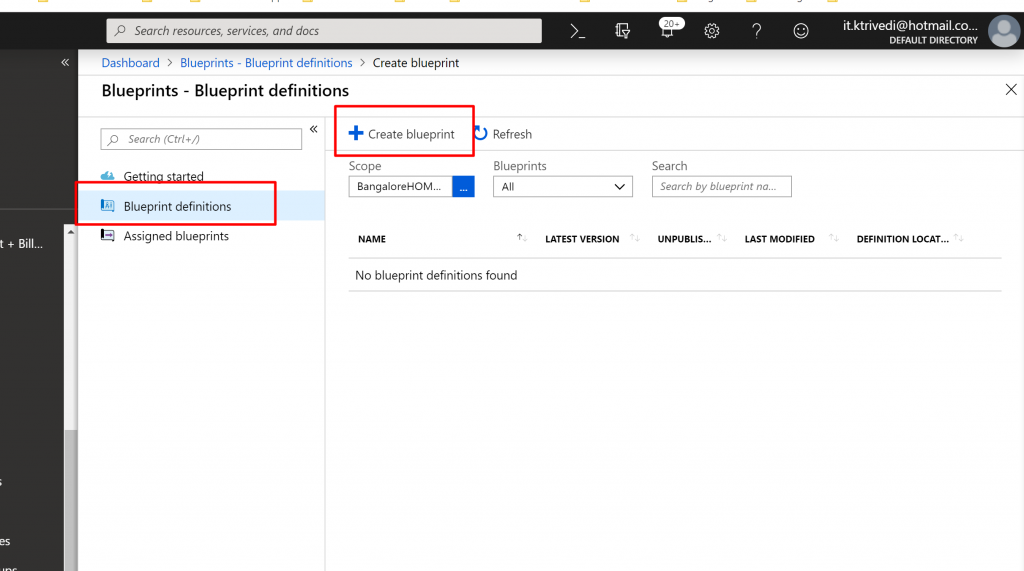
- Select Blueprint definitions from the page on the left and select the + Create blueprint button at the top of the page.
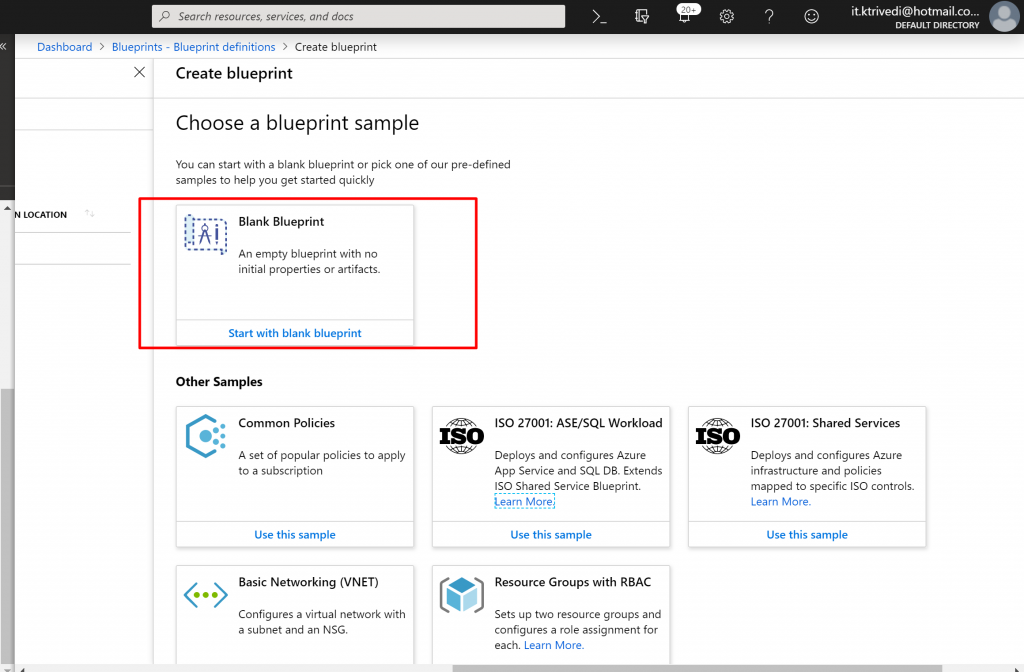
- From the available multiple BluePrints templates select start with Blank Blueprint
- For the definition location box select Management Group name instead of subscription
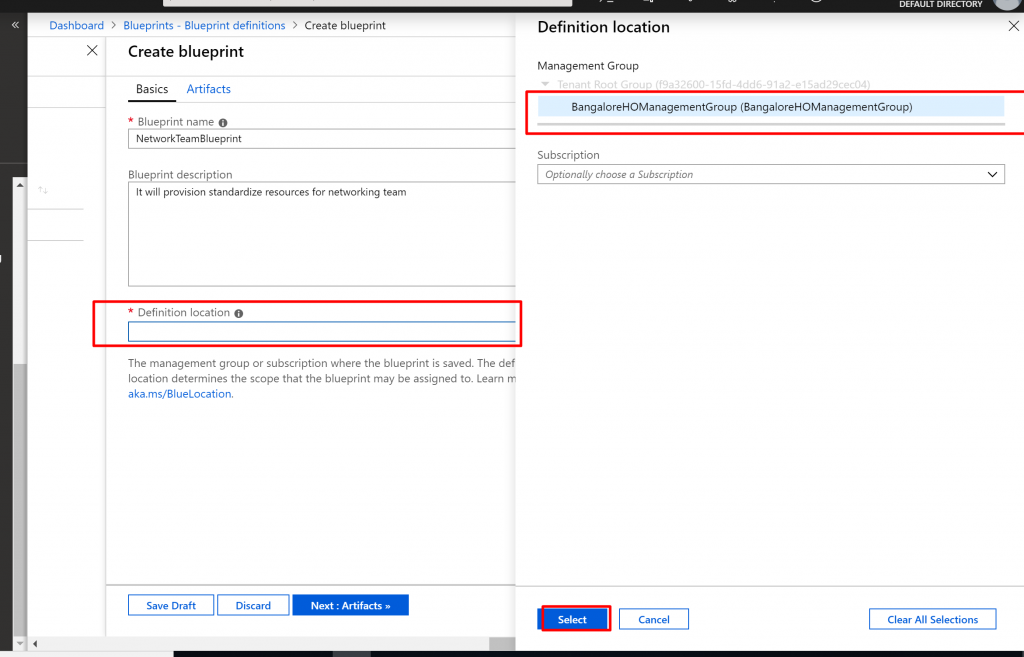
- The Blueprint nameand Definition location fields can’t be changed later. Then select Next : Artifacts at the bottom of the page or the Artifacts tab at the top of the page.
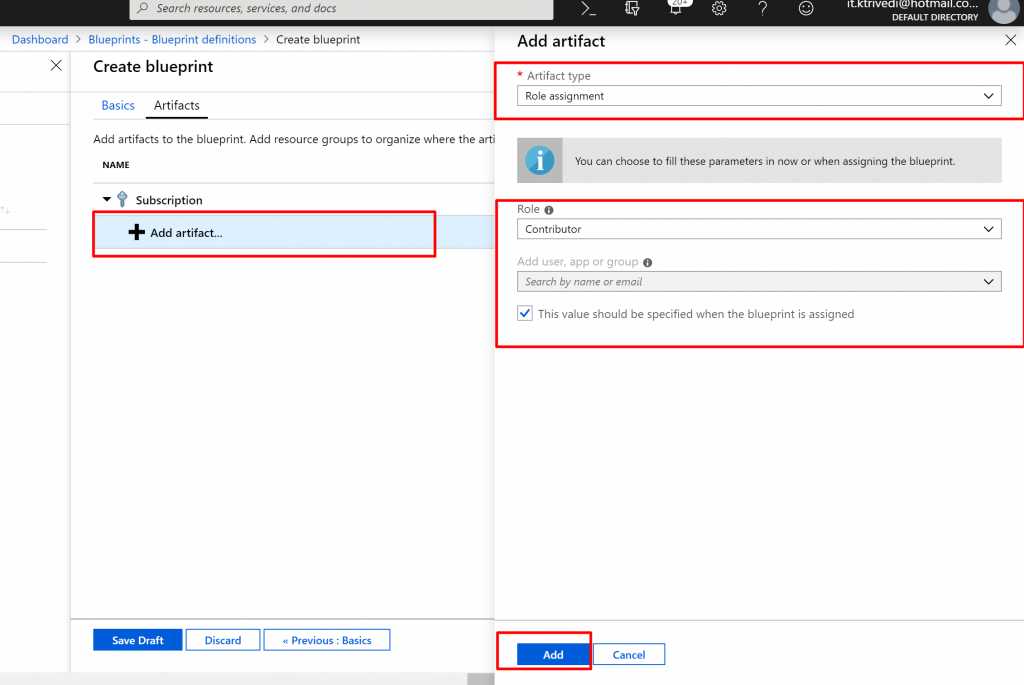
- Add a role assignment at the subscription level:
- Select the + Add artifactrow under Subscription. The Add artifact window opens on the right side of the browser.
- Select Role assignmentfor Artifact type.
- Under Role, select Contributor. Leave the Add user, app or groupbox with the check box that indicates a dynamic parameter.
- Select Add to add this artifact to the blueprint.
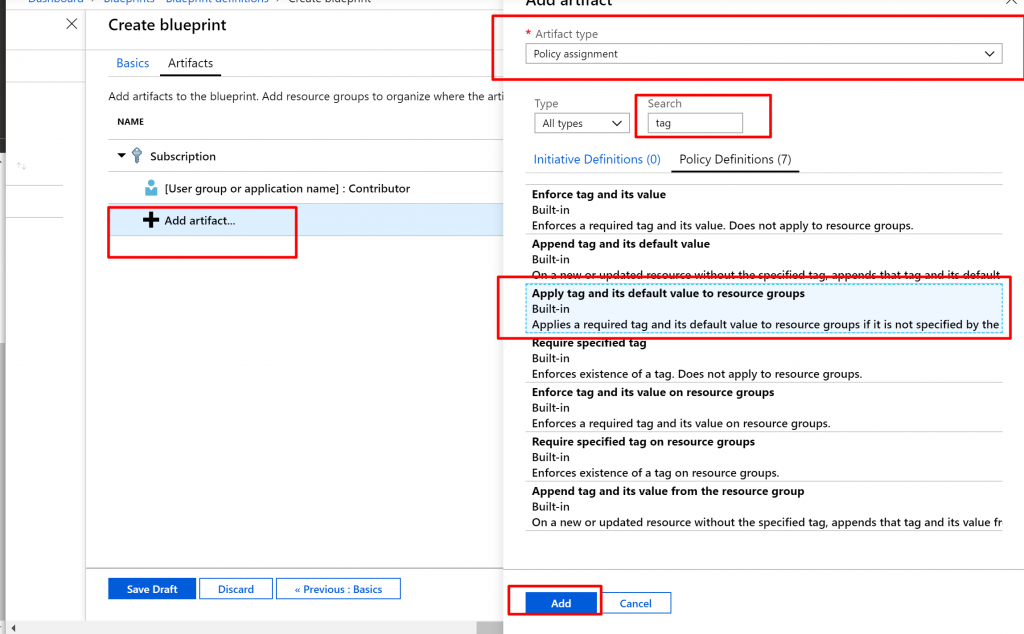
- Add a policy assignment at the subscription level:
- Select the + Add artifact row under the role assignment artifact.
- Select Policy assignment for Artifact type.
- Change Type to Built-in. In Search, enter tag.
- Click out of Search for the filtering to occur. Select Apply tag and its default value to resource groups.
- Select Add to add this artifact to the blueprint.
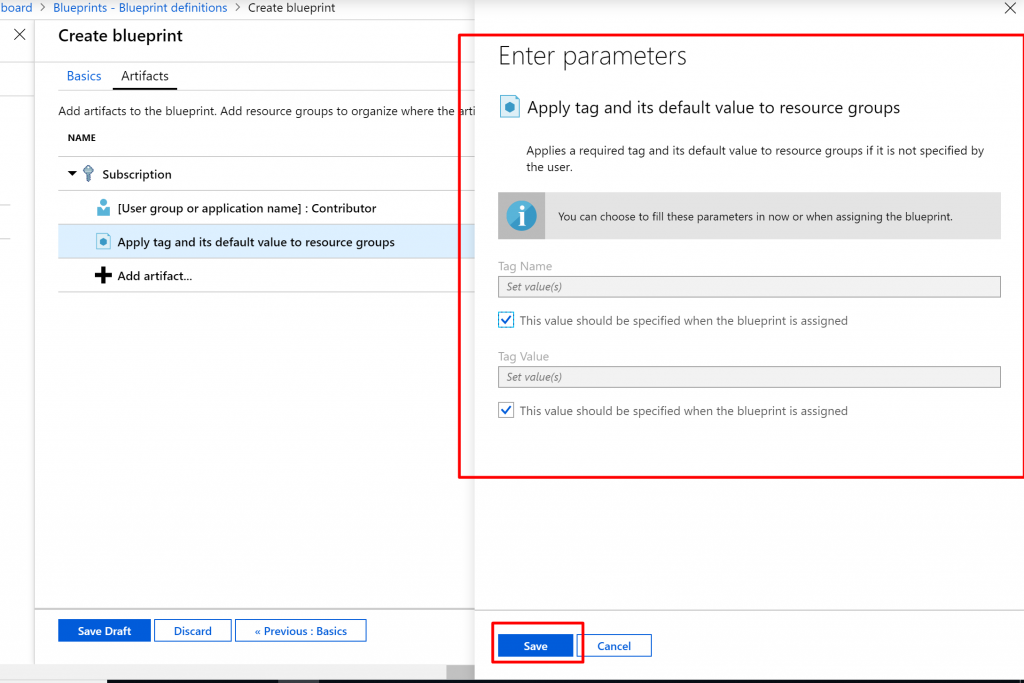
Select the row of the policy assignment Apply tag and its default value to resource groups. The window to provide parameters to the artifact as part of the blueprint definition opens and allows setting the parameters for all assignments (static parameters) based on this blueprint instead of during assignment (dynamic parameters). This example uses dynamic parameters during blueprint assignment, so leave the defaults and select Cancel.
- Add a resource group at the subscription level:
- Select the + Add artifact row under Subscription.
- Select Resource group for Artifact type.
- Leave the Artifact display name, Resource Group Name, and Location boxes blank, but make sure that the check box is checked for each parameter property to make them dynamic parameters.
- Select Add to add this artifact to the blueprint.
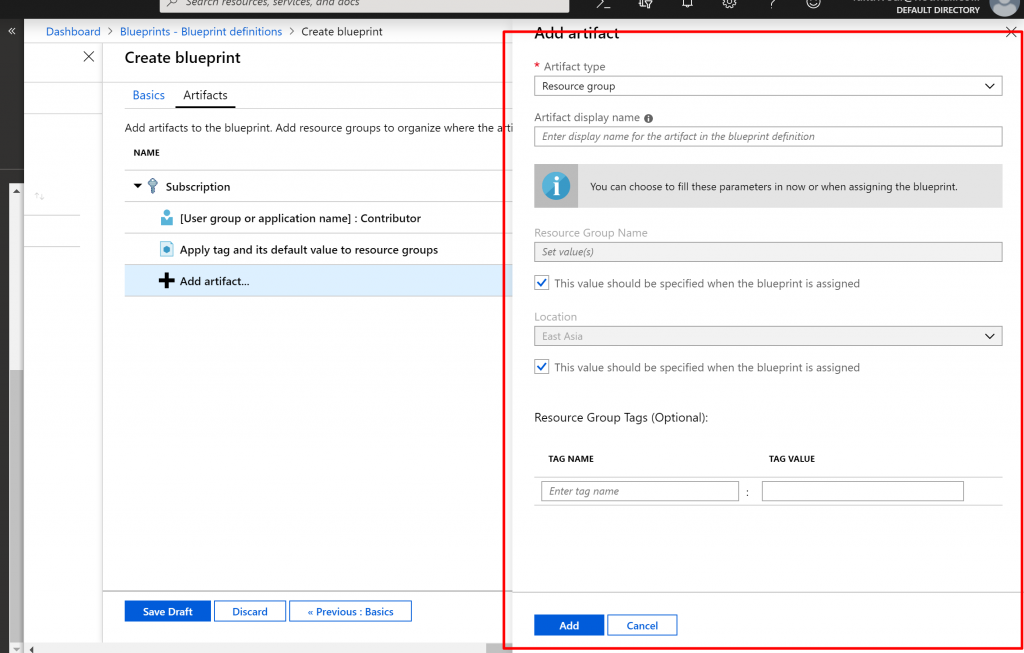
- Select the + Add artifact row under the ResourceGroup
- Select Azure Resource Manager template for Artifact type, set Artifact display name to StorageAccount, and leave Description blank
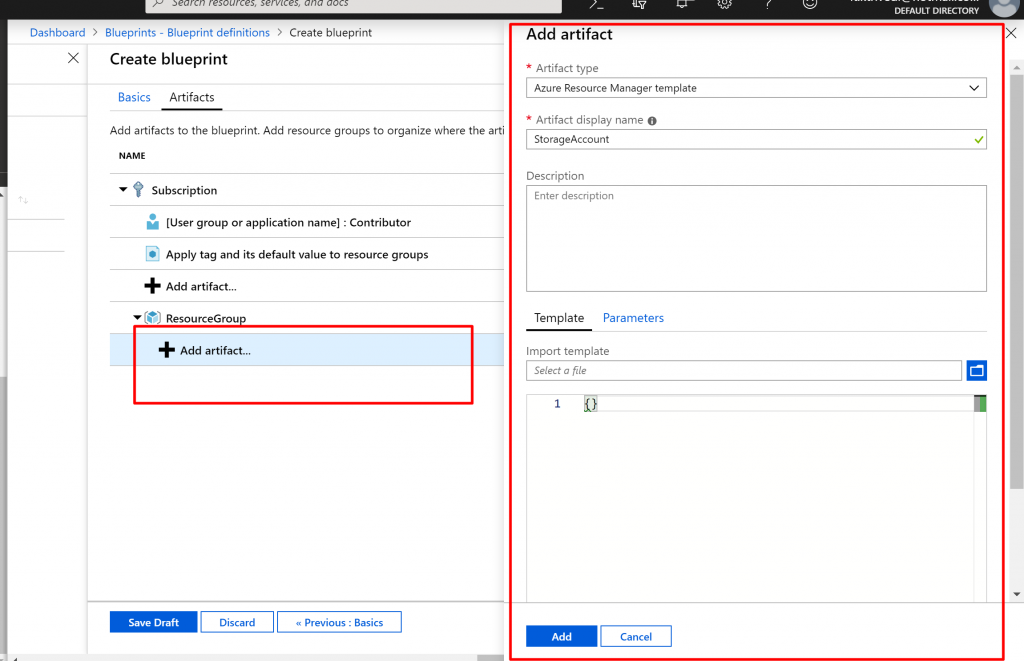
- On the Templatetab in the editor box, paste the following Resource Manager template. After you paste the template, select the Parameters tab and note that the template parameters storageAccountTypeand location were detected. Each parameter was automatically detected and populated, but configured as a dynamic parameter.
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"storageAccountType": {
"type": "string",
"defaultValue": "Standard_LRS",
"allowedValues": [
"Standard_LRS",
"Standard_GRS",
"Standard_ZRS",
"Premium_LRS"
],
"metadata": {
"description": "Storage Account type"
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
}
},
"variables": {
"storageAccountName": "[concat('store', uniquestring(resourceGroup().id))]"
},
"resources": [{
"type": "Microsoft.Storage/storageAccounts",
"name": "[variables('storageAccountName')]",
"location": "[parameters('location')]",
"apiVersion": "2018-07-01",
"sku": {
"name": "[parameters('storageAccountType')]"
},
"kind": "StorageV2",
"properties": {}
}],
"outputs": {
"storageAccountName": {
"type": "string",
"value": "[variables('storageAccountName')]"
}
}
}
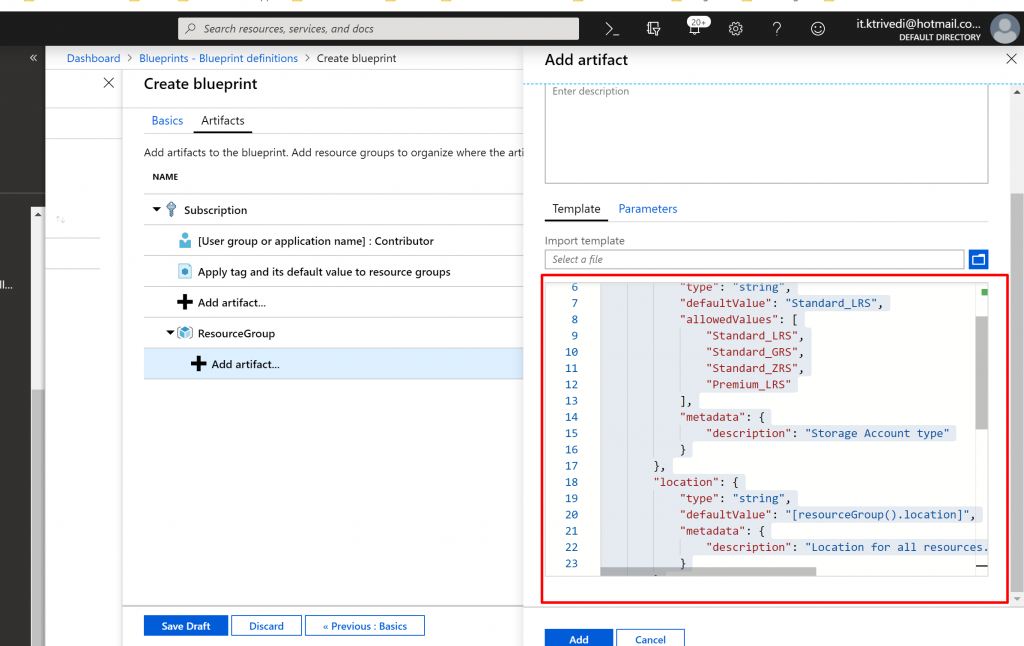
- Clear the storageAccountType check box and note that the drop-down list contains only values included in the Resource Manager template under allowedValues. Select the box to set it back to a dynamic parameter.
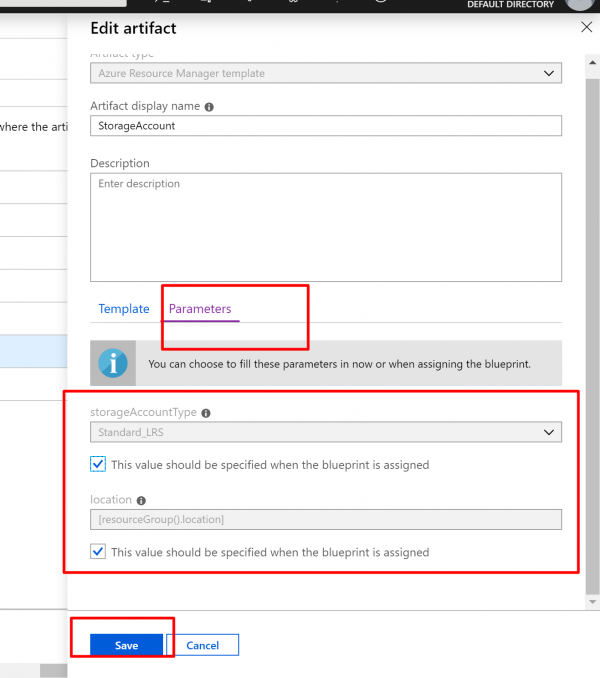
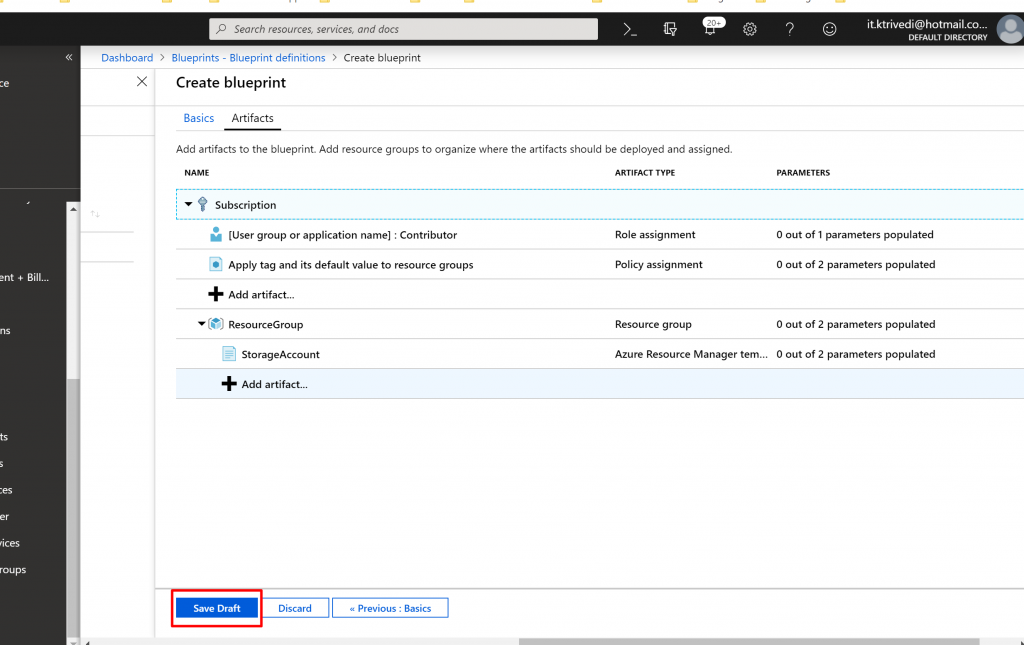
- Your completed blueprint should look similar to the following. Notice that each artifact has x out of y parameters populated in the Parameters The dynamic parameters are set during each assignment of the blueprint.
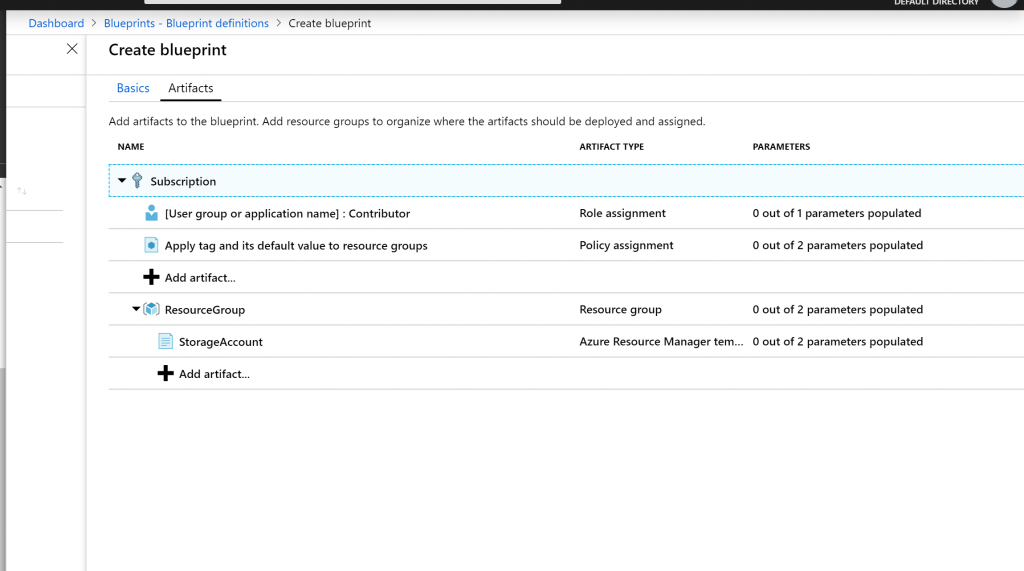
- Click on Save Draft
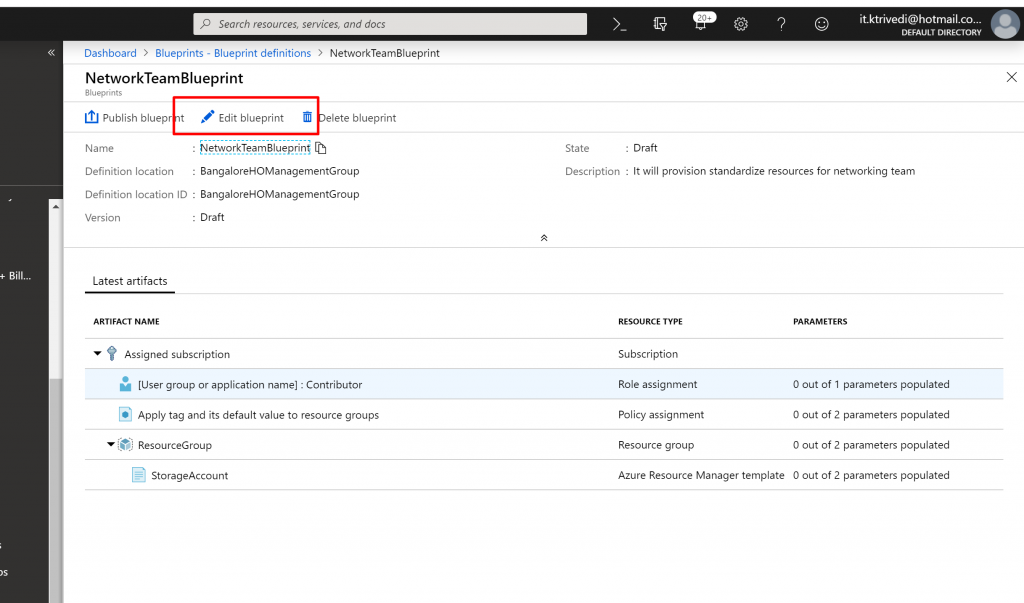
- Click on Edit Blueprint
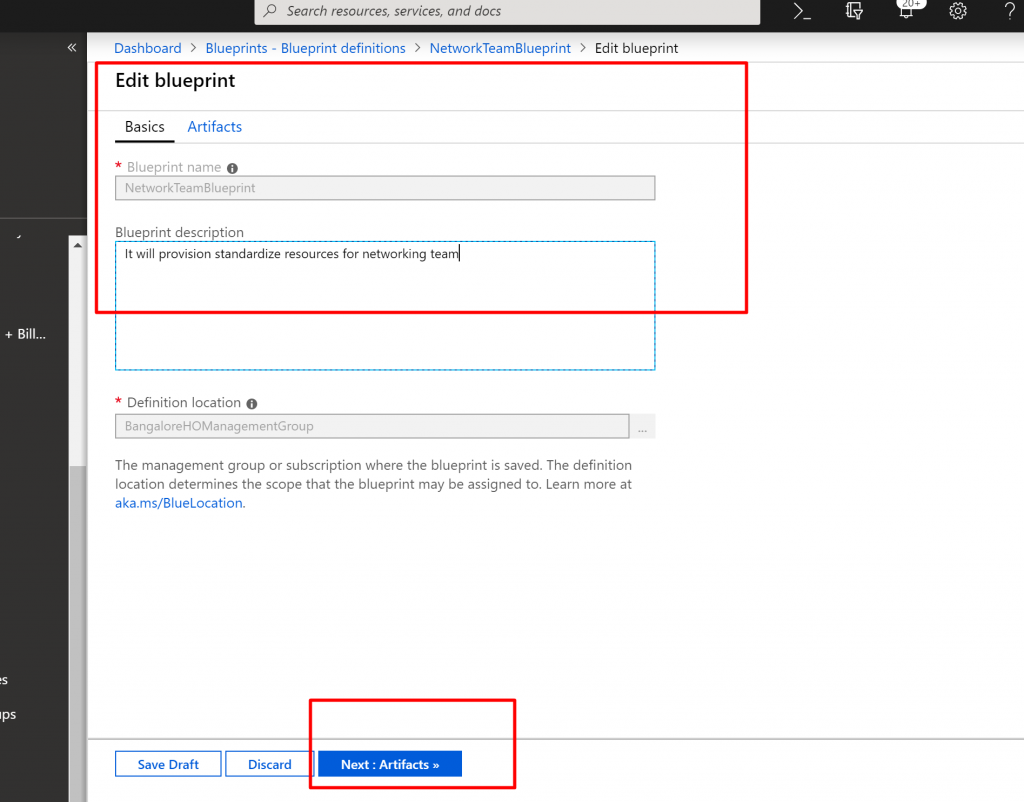
- Select Next : Artifacts at the bottom of the page or the Artifacts tab at the top of the page.
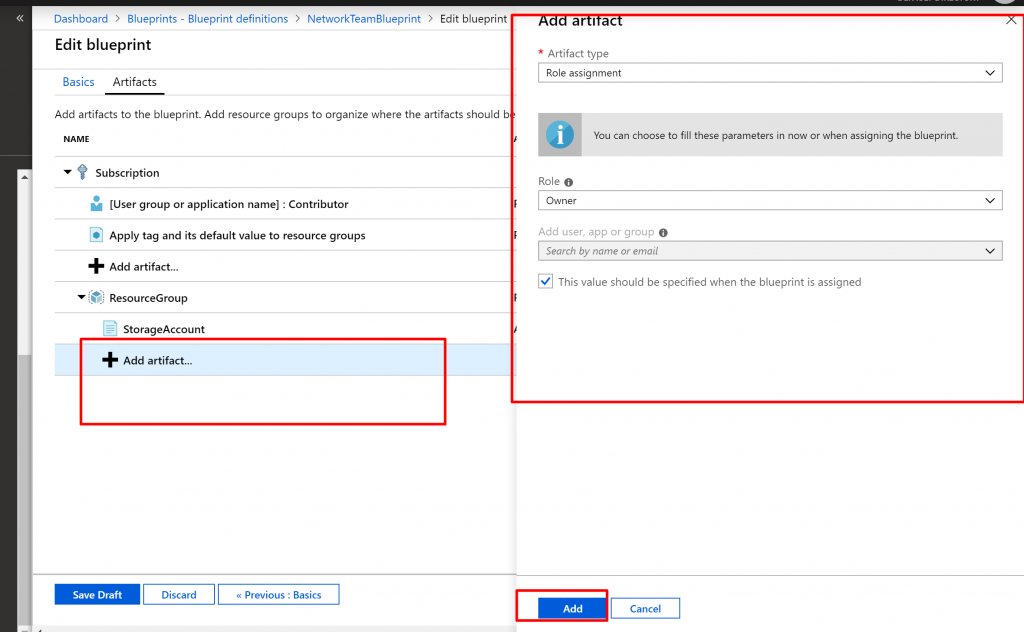
- Add a role assignment under the resource group:
- Select the + Add artifact row directly under the ResourceGroup
- Select Role assignment for Artifact type.
- Under Role, select Owner, and clear the check box under the Add user, app or group
- Search for and select a user, app, or group to add. This artifact uses a static parameter set the same in every assignment of this blueprint.
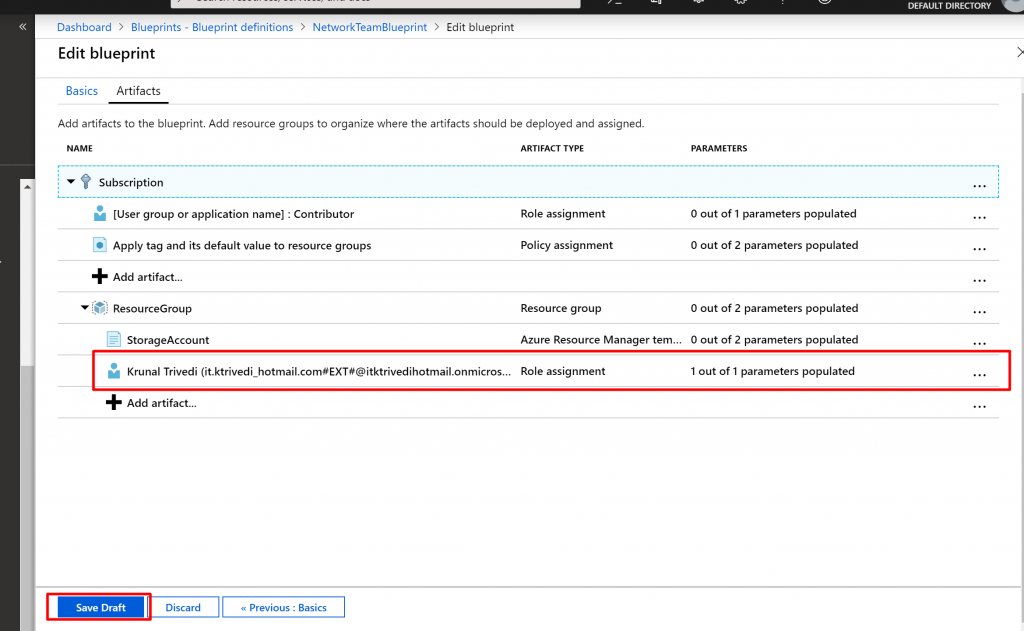
Your completed blueprint should look similar to the following. Notice that the newly added role assignment shows 1 out of 1 parameters populated. That means it’s a static parameter.
Publish a blueprint
Now that all the planned artifacts have been added to the blueprint, it’s time to publish it. Publishing makes the blueprint available to be assigned to a subscription.
- Select Blueprint definitions from the page on the left.
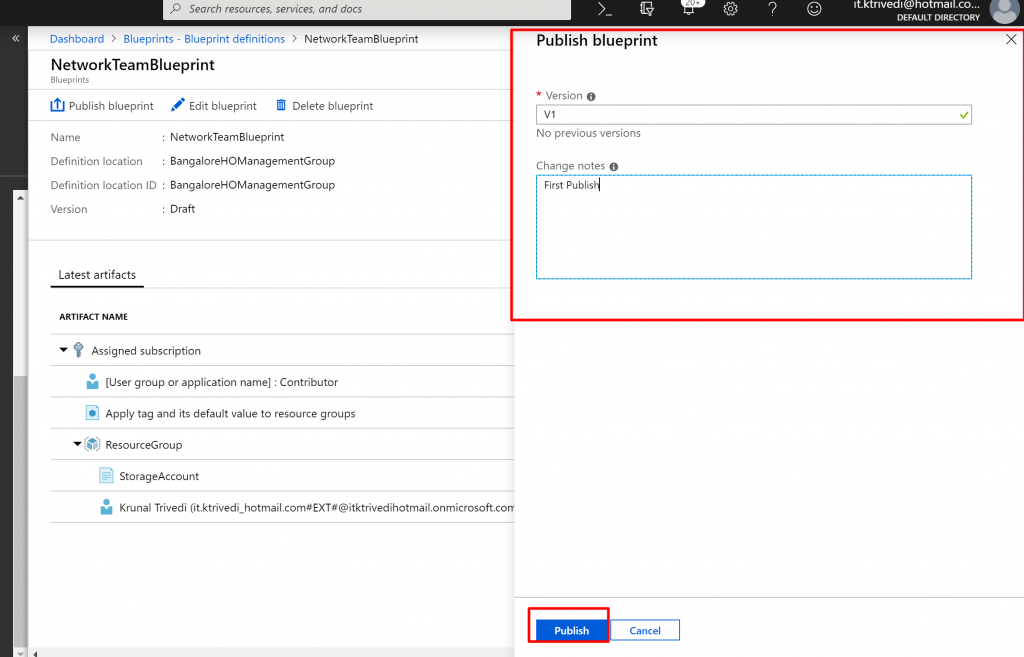
- In the list of blueprints, right-click the one you previously created and select Publish blueprint.
- In the pane that opens, provide a Version(letters, numbers, and hyphens with a maximum length of 20 characters), such as v1. Optionally, enter text in Change notes, such as First publish.
- Select Publish at the bottom of the page.
- Assign a Blueprint
After a blueprint has been published, it can be assigned to a subscription. Assign the blueprint that you created to one of the subscriptions under your management group hierarchy. If the blueprint is saved to a subscription, it can only be assigned to that subscription.
- Select Blueprint definitions from the page on the left.
- In the list of blueprints, right-click the one that you previously created (or select the ellipsis) and select Assign blueprint.
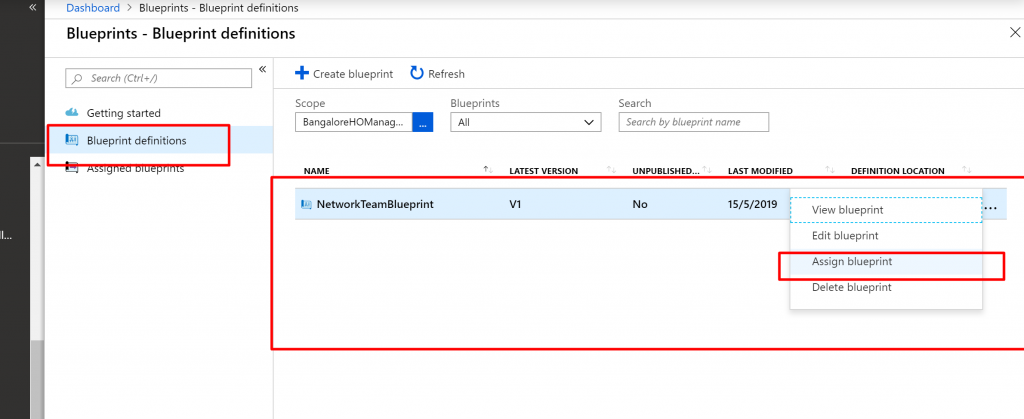
- On the Assign blueprintpage, in the Subscription drop-down list, select the subscriptions that you want to deploy this blueprint to.
- For Assignment name, provide a unique name for this assignment.
- In Location, select a region for the managed identity and subscription deployment object to be created in. Azure Blueprint uses this managed identity to deploy all artifacts in the assigned blueprint.
- Leave the Blueprint definition versiondrop-down selection of Published versions on the v1 (The default is the most recently published version.)
- For Lock Assignment, leave the default of Don’t Lock
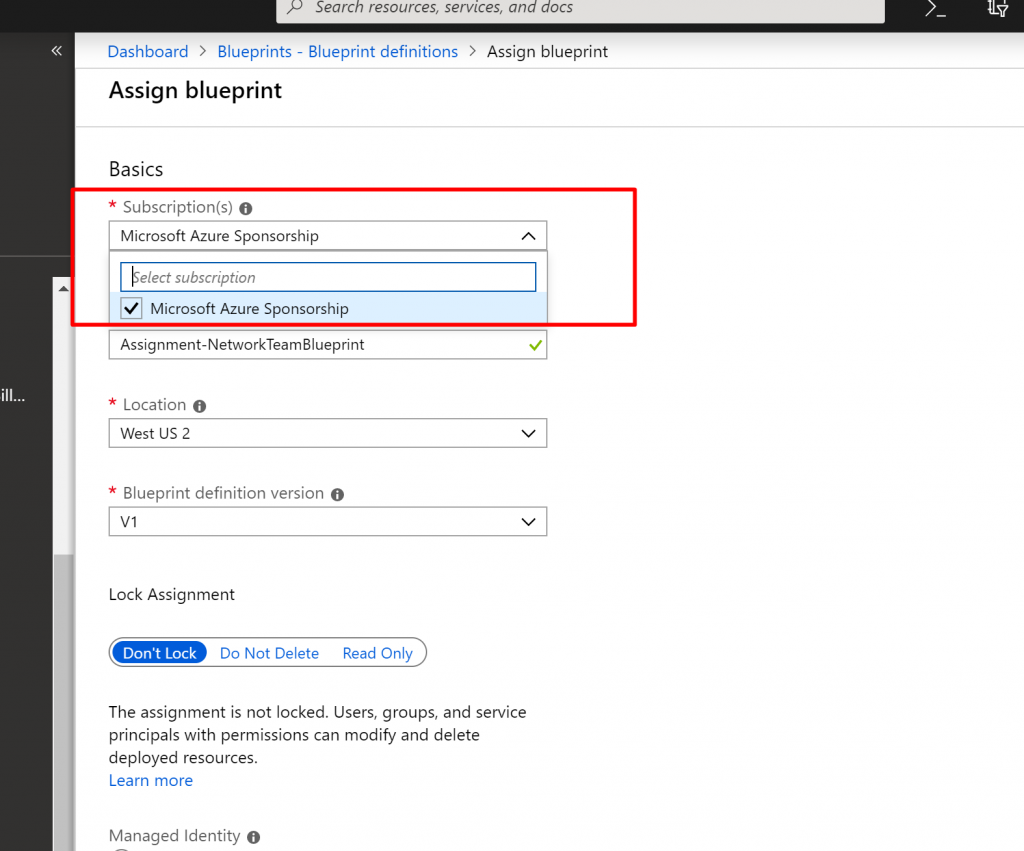
- Under Managed Identity, leave the default of System assigned.
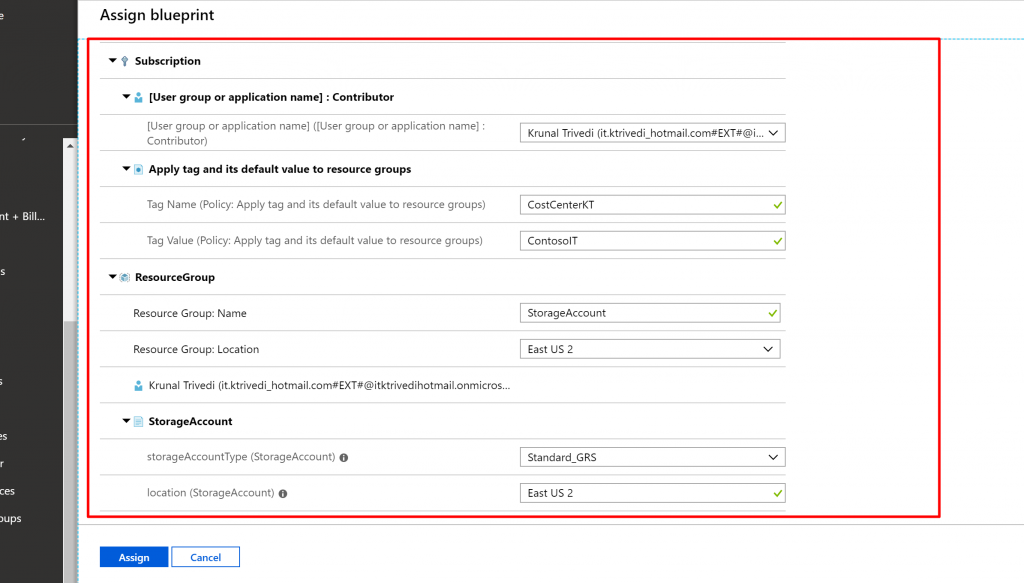
- For the subscription level role assignment [User group or application name] : Contributor, search for and select a user, app, or group.
- For the subscription level policy assignment, set Tag Name to Cost Center and the Tag Value to Contoso IT.
- For Resource Group, provide a Name of Storage Account and a Location of East US 2 from the drop-down list.
Track deployment of a blueprint
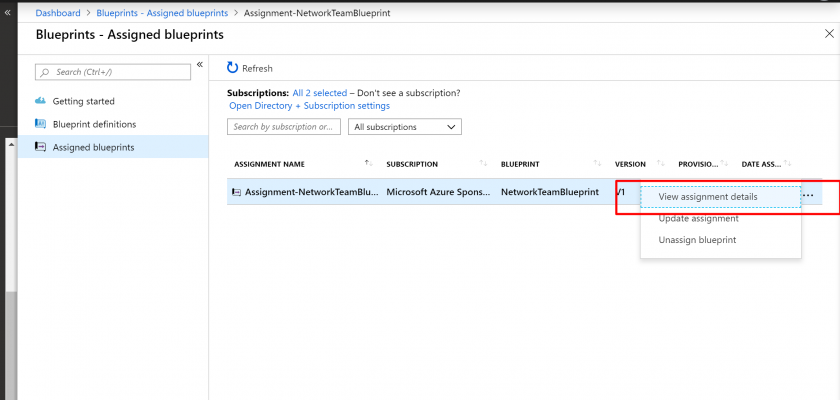
- Select Assigned blueprints from the page on the left.
- In the list of blueprints, right-click the one that you previously assigned and select View assignment details
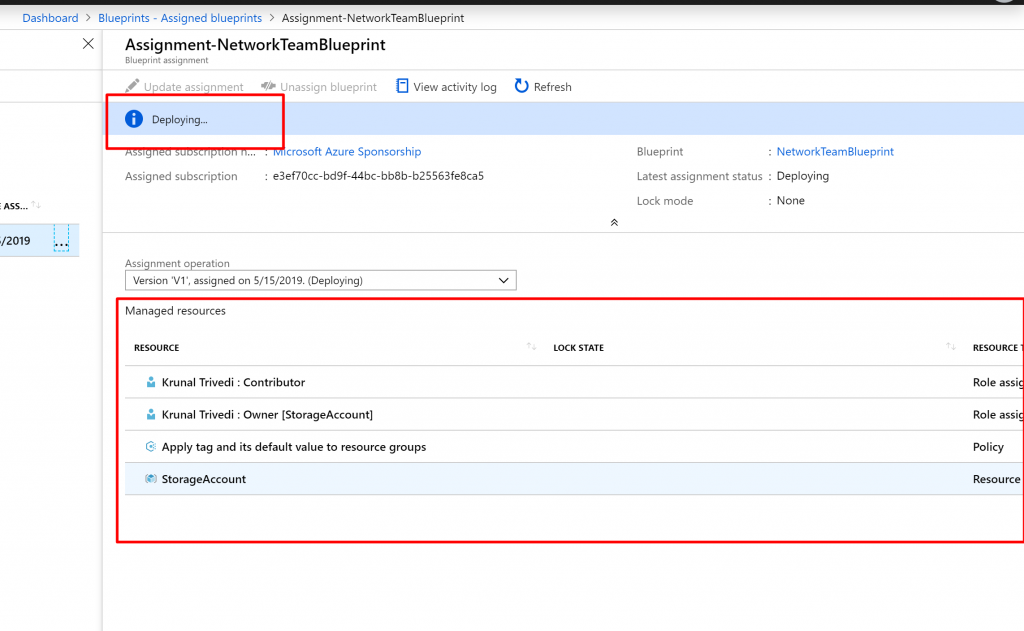
Unassign a blueprint
If you no longer need a blueprint assignment, remove it from a subscription. The blueprint might have been replaced by a newer blueprint with updated patterns, policies, and designs. When a blueprint is removed, the artifacts assigned as part of that blueprint are left behind. To remove a blueprint assignment, follow these steps:
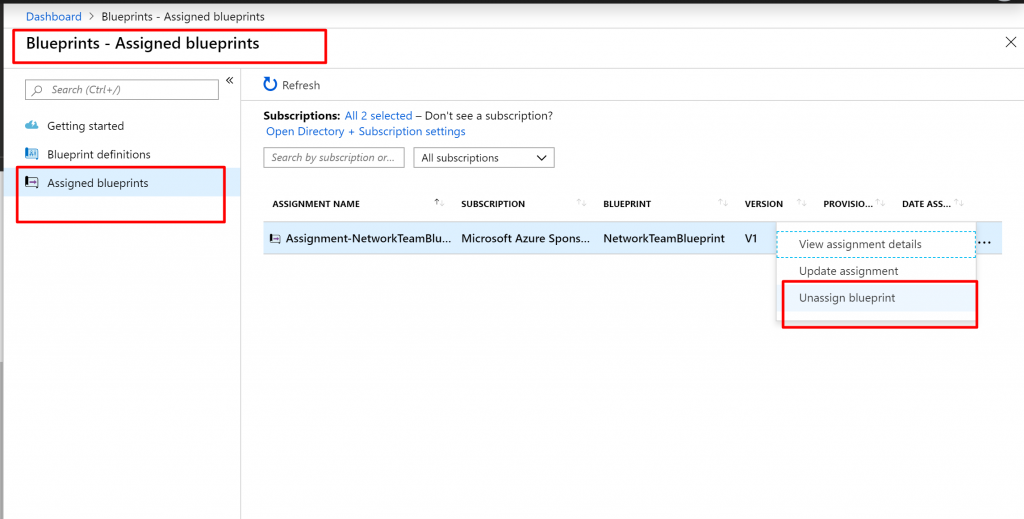
- Select Assigned blueprints from the page on the left.
- In the list of blueprints, select the blueprint that you want to unassign. Then select the Unassign blueprint button at the top of the page.
- Read the confirmation message and then select OK.
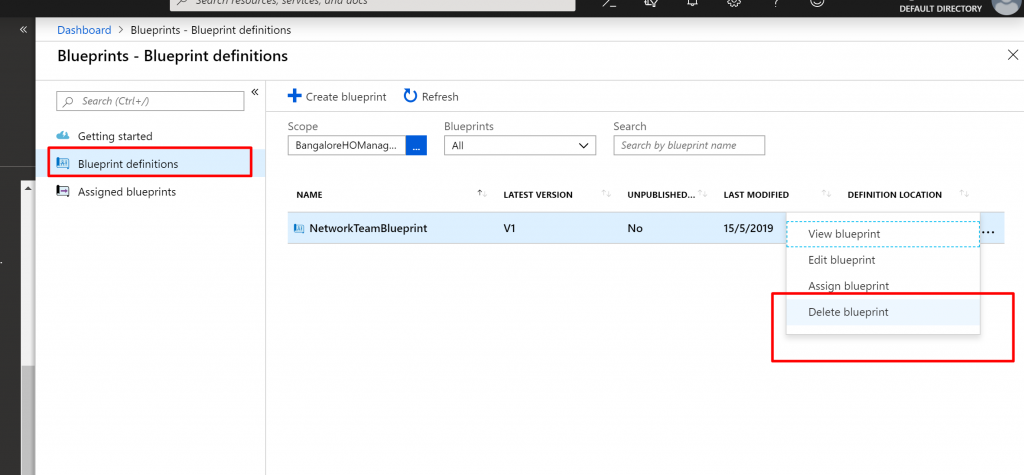
Delete a blueprint
- Select Blueprint definitionsfrom the page on the left.
- Right-click the blueprint that you want to delete, and select Delete blueprint. Then select Yes in the confirmation dialog box.