USING SECURE CONFIGURATION TO STORING SECRETS IN AZURE KEY VAULT AND READING THEM IN AZURE FUNCTIONS – PART 2

This is in continuation with the post Using Secure Configuration with Azure Functions and Azure Key Vault: Part 1. You can find part 1 by clicking this link.
In part one, we create the Azure Function using Visual Studio Code. In this part, we are going to take that ahead and create Azure Key Vault on the Azure Portal. Let’s go ahead and see that.
Go to Azure portal and search for Azure Key Vault. We are going to create that next.
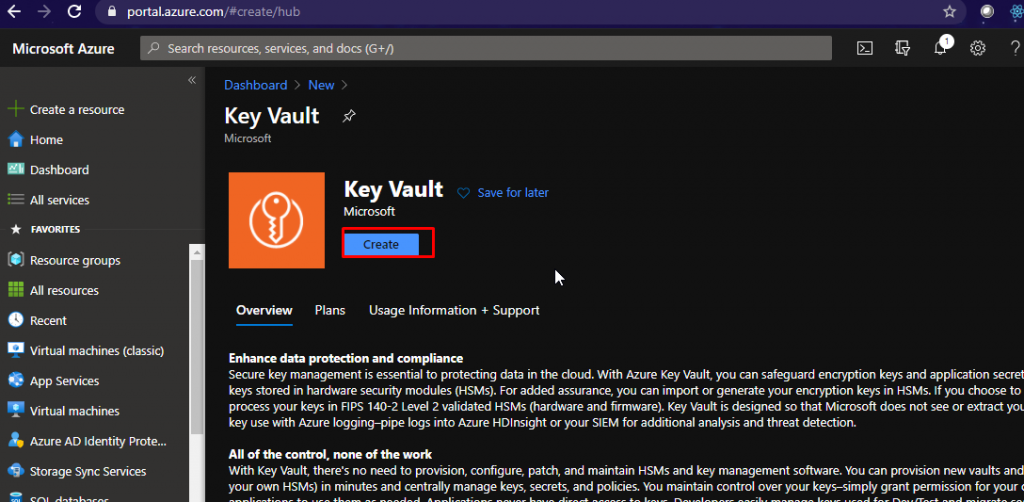
Choose the same resource group as your function app. Give your vault a name. Choose the region. Keep all the other settings as they are and create it.
Your function app must have published too by now. Go to it and go to Identity in it. Here, we can create an Azure Managed Service Identity for our Azure Function. We are going to use this to connect to Azure Key Vault without needing API keys.

Change the status to On and click Save. On the next prompt, choose yes.

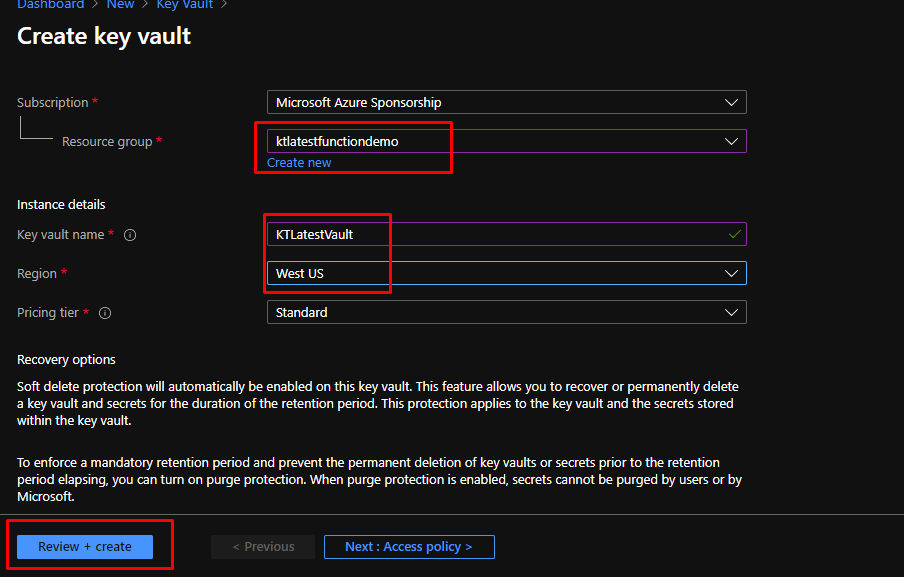
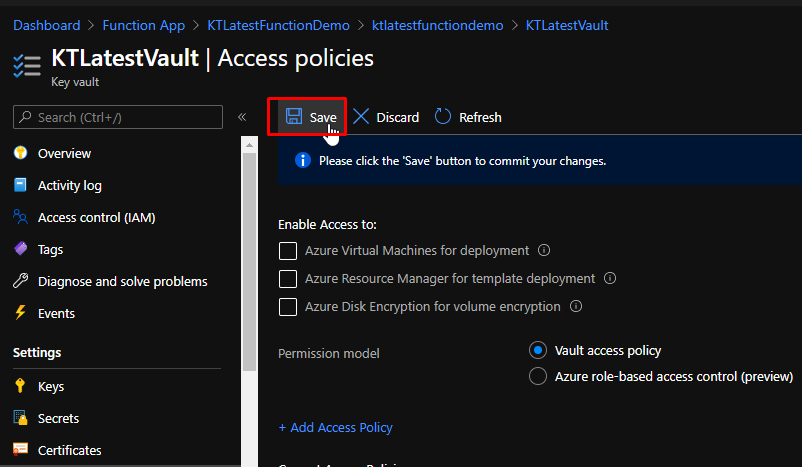
Next, go to the Key vault and go to Access policies. Click Add Access Policy.
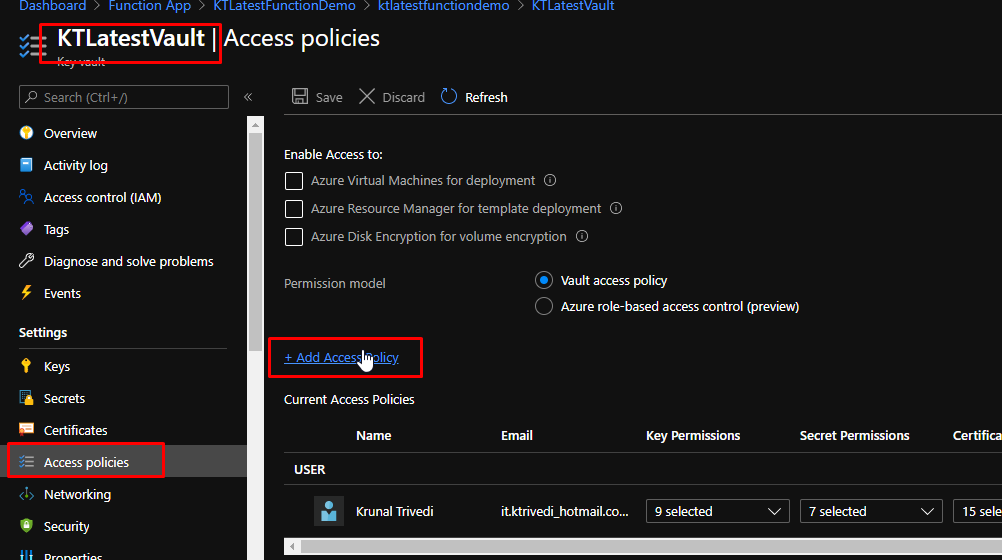
Add the Managed Service Identity principal from the list for your key vault. Then, select all the permissions so that you can experiment with whatever you want to with your Azure Key Vault. Click Add.
Finally, click save.
Then, we are going to add a secret. Go to Secrets and click Generate.

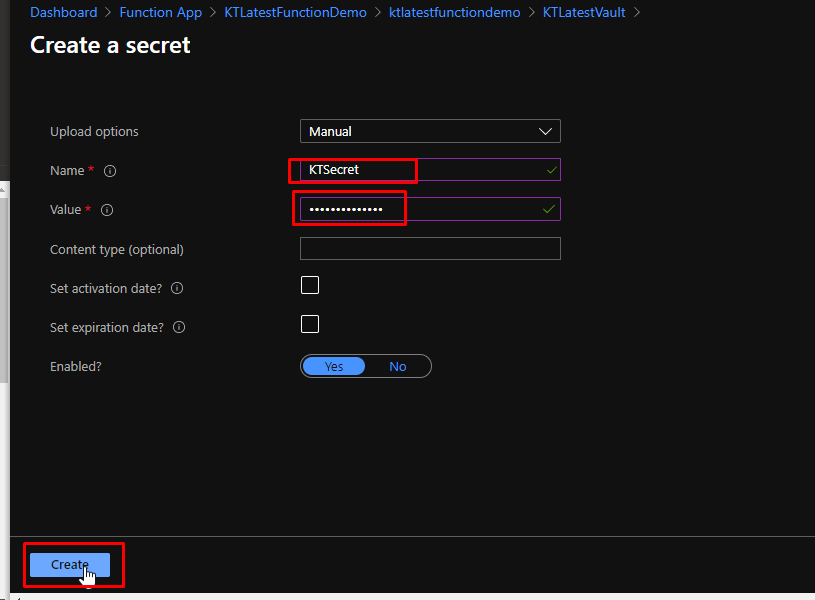
Give your secret a name and add some value to it. Click Create.
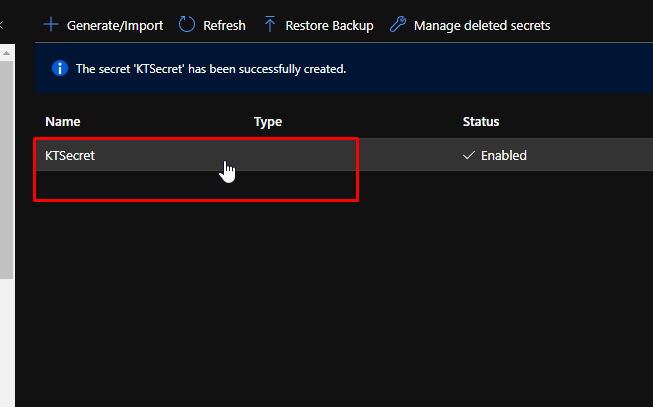
Once the secret gets created, go to it.
When you open it, you will see that it has one version. Click on it.
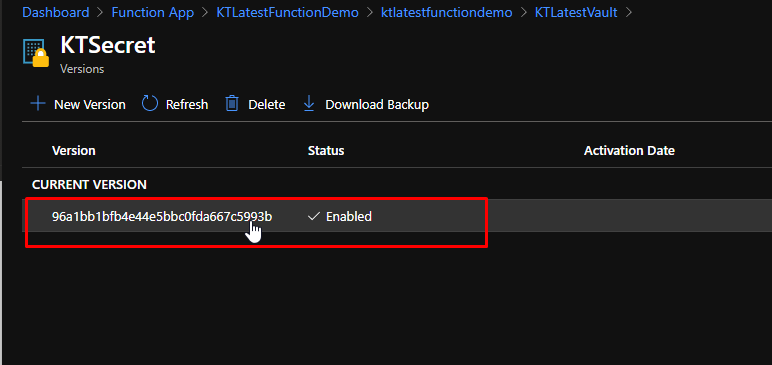
From here, we need the secret identifier. So copy it and keep it aside for some time.

Now go back to the function app and go to configuration. Here, we are going to add a new application setting.

For the name, I am going to use the same one as my secret name. However, this can be anything. The name has no connection to it. But, the value has.
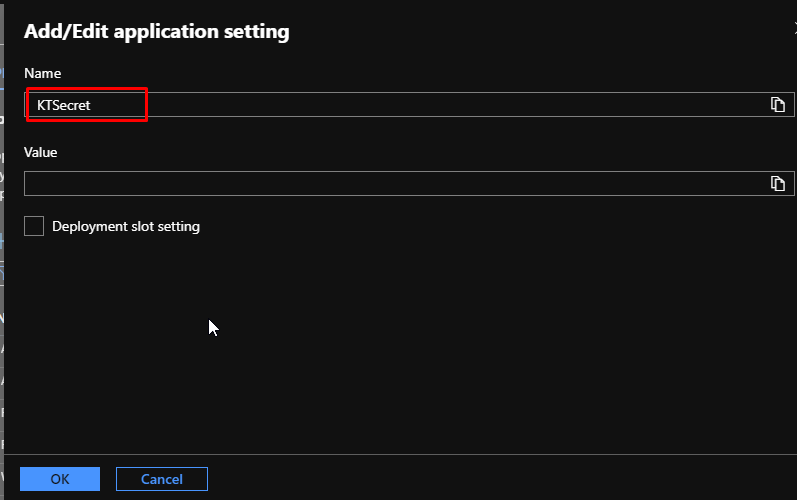
For the value, we are going to add this. @Microsoft.KeyVault(SecretUri=“YourSecretIdentifier”)

- This way, we don’t have to connect to the Key Vault in any way. Because we use this format along with the managed service identity, things get easy for us.
Click Save. And on the next prompt, click Continue.
To test it, go to the function app and run it. If it runs successfully, you will see the secret value in your logs.

- That is it. You can go ahead and try to yourself.